We were around 9-10 people and I was the person meeting them for the 1st time. I don't know about others but I was completely blank what was actually going on and what was the thing they were talking about. So I recommend you to go through this small list before you go to any kind of hackers meetup. Well you can consider this as the 1st step into infosec that is Information Security.
WWW:
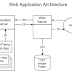
Its a short abbreviation of World Wide Web, The web. All the users using HTTP and are globally connected to each other. The WWW is one of many applications of the network.
It is based on the following technologies:
- Webserver
- HTML
- HTTP
- and a Web Browser
HTTP & HTTPS:
HTTP is Hyper Text Transfer Protocol and HTTPS stands for Hyper Text Transfer Protocol Secure which are nothing but are application protocols that directs the network to decide how the documents should be displayed to you. HTTPS sends the data in encrypted form which means the data is not sent in plan text. These protocols needs a web browser to display the files. HyperText are text with a link directing to another text or document with its web address. There are many other protocols so here I am sharing a small list of protocols if you are further interested in.
SSL:
SSL is Secured Socket Layer which is a cryptographic protocol that make sure that the data is transferred from a browser to the destination server without any data manipulation and remains integral. To know about the working of SSL do check this link.
Kernel:
Kernel is a computer program which manages the hardware and convey the process to be performed for the OS. Here you can find linux kernel Archive as Linux is Open Source you can find its kernel
Every OS has its own kernel. Moding a kernel in a correct way can add some new features to your OS.
Linux:
Linux is an operating system created by Linus Torvalds. He evolved linux from an kernel because a kernel by itself gets you nowhere. To get a working system you need a shell, compilers, a library etc.
Linux is open source and is distributed under GNUv2 and GPL licensing.
Shell:
A shell is a user interface which is/was used to interact with your operating system. It need particular commands to interact. There are many types of shell like Cshell, the Bourne shell, and the Korn shell. It is a part of command processor which runs based on the given input by the user. It verifies that the command is valid or not. If valid it sends the commands to another part of process.
Linux Distributions:
Linux distributions also called as Linux Distro are different different linux os based on different different DE(Deskstop Environment) loaded with software's and own built linux kernel. Kali, SamuraiSTF and Blackbuntu are some of the penetration testing linux distro's.
Vulnerability:
A vulnerability is a weakness in a web application or in a network protocol or a cartography algorithm or a lock or a safe.
Exploit:
Taking advantage of that vulnerability is exploitation. Using that vulnerability with actually breaking into the system or anything is called Exploitation. It is not always necessary that a vulnerability is exploitable. Exploitation can be in any form, like any programming language or can be a video or step by step procedure. This is Exploit or generally called a POC(Procedure Of Conduct).
Payload:
Things done after exploiting a system is called payload. Payload is again a code which is with exploit code so, as soon as an exploit is successful the payload takes the charge and start it's work like connecting the system back to the attacker or executing a Malware or simply fetch the credentials. The Payload completely depend on the attacker what he/she wants to do.
Penetration Testing:
It is a way to test security of a web application or a network or a system methodically validating
and verifying security mechanism implemented on it.
This doesn't include only the above but also a proper reporting is to be done.
CVE:
CVE stands for "Common Vulnerabilities and Exposure" which maintains the list of Vulnerability reported and maintained it with a specific ID that would help in recognizing the vulnerability.
The main aim is to standardize names of the publicly known vulnerabilities.
You can get further information about lots and lots of terms related to security I am sharing:
OUSPG
NIST[PDF]
Sans Glossary