Poison was one of the machine in hack the box and got retired few minutes back. It was my first box and took me a bit long to root this for no reason. Why Poison was my first box? Because I had to start with something really easy just because I get some confidence to play. Well, lets get started.
Getting Started:
I initiated with nmaping on the box. Lets find top 10 ports in nmap-services using --top-ports flag.
More other options can be used to determine open and running ports but this is usually I use for quick results.
As can be seen in the above screenshot, port 22 and 80 are open. I quickly went to my browser and this is what I found.
They had already given some filenames which I tried. On trying them, I observed a URL pattern which smells fishy. It was like this, http://10.10.10.84/browse.php?file=ini.php. I was able to view the content of the file. Lets try /../../etc/passwd instead of ini.php
Awesome! Its LFI. Noted. For now lets move on to other files we already know and explore their content.
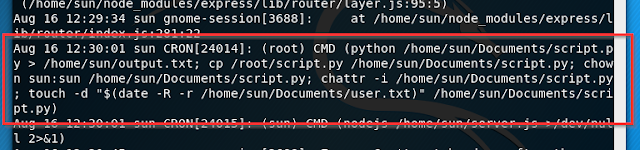
All the files had some or the other php array but listfiles.php was listing out current directories files which had an interesting file with name pwdbackup.txt.
This string looks like base64. On decoding the the string 13 times "Charix!2#4%6&8(0" is something I found. This says it all because Charix looks like a username and if you remember, /etc/password had charix as a user on this box but then the question arise, how to login to the system? nmap results says that the box has ssh service. The credentials were correct and here we could successfully login as charix user.This password is secure, it's encoded atleast 13 times.. what could go wrong really.. Vm0wd2QyUXlVWGxWV0d4WFlURndVRlpzWkZOalJsWjBUVlpPV0ZKc2JETlhhMk0xVmpKS1IySkVU bGhoTVVwVVZtcEdZV015U2tWVQpiR2hvVFZWd1ZWWnRjRWRUTWxKSVZtdGtXQXBpUm5CUFdWZDBS bVZHV25SalJYUlVUVlUxU1ZadGRGZFZaM0JwVmxad1dWWnRNVFJqCk1EQjRXa1prWVZKR1NsVlVW M040VGtaa2NtRkdaR2hWV0VKVVdXeGFTMVZHWkZoTlZGSlRDazFFUWpSV01qVlRZVEZLYzJOSVRs WmkKV0doNlZHeGFZVk5IVWtsVWJXaFdWMFZLVlZkWGVHRlRNbEY0VjI1U2ExSXdXbUZEYkZwelYy eG9XR0V4Y0hKWFZscExVakZPZEZKcwpaR2dLWVRCWk1GWkhkR0ZaVms1R1RsWmtZVkl5YUZkV01G WkxWbFprV0dWSFJsUk5WbkJZVmpKMGExWnRSWHBWYmtKRVlYcEdlVmxyClVsTldNREZ4Vm10NFYw MXVUak5hVm1SSFVqRldjd3BqUjJ0TFZXMDFRMkl4WkhOYVJGSlhUV3hLUjFSc1dtdFpWa2w1WVVa T1YwMUcKV2t4V2JGcHJWMGRXU0dSSGJFNWlSWEEyVmpKMFlXRXhXblJTV0hCV1ltczFSVmxzVm5k WFJsbDVDbVJIT1ZkTlJFWjRWbTEwTkZkRwpXbk5qUlhoV1lXdGFVRmw2UmxkamQzQlhZa2RPVEZk WGRHOVJiVlp6VjI1U2FsSlhVbGRVVmxwelRrWlplVTVWT1ZwV2EydzFXVlZhCmExWXdNVWNLVjJ0 NFYySkdjR2hhUlZWNFZsWkdkR1JGTldoTmJtTjNWbXBLTUdJeFVYaGlSbVJWWVRKb1YxbHJWVEZT Vm14elZteHcKVG1KR2NEQkRiVlpJVDFaa2FWWllRa3BYVmxadlpERlpkd3BOV0VaVFlrZG9hRlZz WkZOWFJsWnhVbXM1YW1RelFtaFZiVEZQVkVaawpXR1ZHV210TmJFWTBWakowVjFVeVNraFZiRnBW VmpOU00xcFhlRmRYUjFaSFdrWldhVkpZUW1GV2EyUXdDazVHU2tkalJGbExWRlZTCmMxSkdjRFpO Ukd4RVdub3dPVU5uUFQwSwo=
ls command have a file namely 'secret.zip'. While trying to unzip the file, the error was to provide a password to the file. quick google search and got to know that unzip -P
On trying to unzip and crack this locally, found nothing. But wait, I haven't tried what I already have. Lets try the charix password and yes, it did worked locally. On extracting the strange string did not mean anything. Lets leave this for now.
I tried to access /root/root.txt just to make sure I was not having access to it.
Lets try to gather some information about the system:
FreeBSD Poison 11.1-RELEASE FreeBSD 11.1-RELEASE #0 r321309: Fri Jul 21 02:08:28 UTC 2017 root@releng2.nyi.freebsd.org:/usr/obj/usr/src/sys/GENERIC amd64
There are couple of ways to get this information about FreeBSD Version is using uname -a and strings /boot/kernel/kernel | grep RELEASE commands. I tried to find any public exploit available for this FreeBSD version but nothing interesting found. So, freebsd is better at security and usually it is not that easy to gain other privilege over such BSD systems.
I tried to search for file name with the string 'password' using find / | grep 'password'. Found some interesting files and on analyzing them did not come up with what was required.
Finding some root internal service which can also reveal something good.
So lets see the running processes which is running on the machine with a ps aux.
We can see some processes running under root privileges. Nothing interesting except a single service, vnc. Yes, this is something I should try to exploit.
But wait, this wasn't found in nmap. Why was this even a service running, when it was supposed to be accessible from outside?? On searching more about this, I got to know that it was possible to create an ssh tunnel to any port.
https://www.cl.cam.ac.uk/research/dtg/attarchive/vnc/sshvnc.html
The above article says VNC to make more secure. but now, how this could be exploited? We have the service internally running as a root. Somehow if we can access vnc would be great as it will give a root access directly. We somehow need to run commands on vnc connecting with vnc. So let us create an ssh connection to vnc which is already running as a root.
We are getting connected as charix and after logging in, nothing happens. It is simply creating a coonection to the port and that is it. After sometime, it struck me that when we are connected as ssh, we are exposing internal services to the host. All it require is a way to access vnc. Do we have something? vncviewer is something which should work.
It ask for the password. We do have a pass file. On a bit of searching I found that it was possible to provide password from a file. I tried doing the same on the file directly.
As soon as this, a popup with a shell I could see..
I hope you all enjoyed the article. Share it if you liked it.. :)