SPOILER ALERT!!
Celestial was pretty straightforward. It was not as easy as Poison to achieve user access. Though root was pretty easy. Celestial made me do alot of different things and in the process learned alot of new things. This is the advantage of Hack The Box as well as other vulnerable machines and CTF.
As we can see, there is only one port available. After a bit of searching got to know that this is used for nodejs. This is how it looks like when opened up on browser.
Error!! I tried to change rce in the format to dummy but soon realized that this is the correct format and this is how the application should respond.
Payload
Why not have a serialized format there to make it execute the way we want? Lets run some nodejs based shell. nodejsshell.py can help us with thi.
The payload is ready all you have to do is to place it in the serialize formatted function between {"rce":"_$$ND_FUNC$$_function (){\n \t [code] \n }"}
and
It did not took me long to go to Documents to find the user flag but a thing to notice that Documents also had a python script named as script.py which was getting updated every 5mins. It had a single line of code saying, script is running. I remembered it clearly there was an output.txt file there on the user's root folder.
On checking the contents it was printing the output of script.py file. I also recognized that the permissions given to the file was root only.
I wrote a small python script in script.py
Believe me, I was literally waiting for 5mins.
This is enough to make it clear that we could now run anything as root. I even got a reverse shell though by just providing a python based reverse shell. To know, what exactly was going on, I thought to check out the logs.
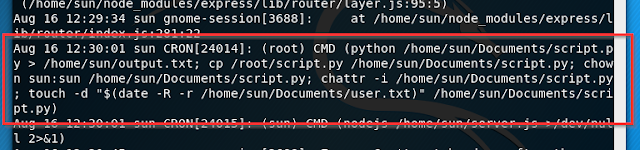
There was this cronjob responsible to execute the script.
I Hope you enjoyed the article. Please share and comment.
Celestial was pretty straightforward. It was not as easy as Poison to achieve user access. Though root was pretty easy. Celestial made me do alot of different things and in the process learned alot of new things. This is the advantage of Hack The Box as well as other vulnerable machines and CTF.
Lets Get Started:
The machine was little unstable as sometimes I could not even connect to it and was loosing connection frequently due to some reason. To start, lets nmap to see what are the open ports. Initially for a normal scan, I didn't find anything but after few more scans, I found one open port and below are the results:
As we can see, there is only one port available. After a bit of searching got to know that this is used for nodejs. This is how it looks like when opened up on browser.
404? Well I tried to enumerate directories but was showing error i.e no GET request defined for the application but soon this grabbed my attention:
Well, this can be a hint but no. I wondered, how this came up? May be because someone did a mischief? No. It struck me first about expression injection based on this. Soon I realized that there must be some kind of session used. This came up when I refreshed it again. Whenever a new user land on this page, 404 was shown, though it wasn't 404 Error and as soon as refreshed, the application gives session to the user. The session was base64 encoded.
This again looks like a hint. I thought, lets change the use to another use and again encode it with base64 and provide the application, a rough session id by changing the username to admin. No results, so I tried playing with this json and something I came across.
This Error caught my attention. So now we have something related to nodejs serialization. Is there any vulnerability related to serialization in nodejs? Yes! Deserialization to RCE.
Some of the programming languages have serialization function to convert data into an object. There are various reason to serialize something. When a nodejs data is been serialized it looks something like this.
{"rce":"_$$ND_FUNC$$_function (){\n \t [Code] \n }()"}
This can be seen when a function is converted into a serialized format. We already knew that the application is taking a serialized data to it. I tried to run this to know if this works for me before even trying to exploit.Error!! I tried to change rce in the format to dummy but soon realized that this is the correct format and this is how the application should respond.
Payload
Why not have a serialized format there to make it execute the way we want? Lets run some nodejs based shell. nodejsshell.py can help us with thi.
The payload is ready all you have to do is to place it in the serialize formatted function between {"rce":"_$$ND_FUNC$$_function (){\n \t [code]
and
It did not took me long to go to Documents to find the user flag but a thing to notice that Documents also had a python script named as script.py which was getting updated every 5mins. It had a single line of code saying, script is running. I remembered it clearly there was an output.txt file there on the user's root folder.
On checking the contents it was printing the output of script.py file. I also recognized that the permissions given to the file was root only.
I wrote a small python script in script.py
Believe me, I was literally waiting for 5mins.
This is enough to make it clear that we could now run anything as root. I even got a reverse shell though by just providing a python based reverse shell. To know, what exactly was going on, I thought to check out the logs.
There was this cronjob responsible to execute the script.
I Hope you enjoyed the article. Please share and comment.